Advanced Login Introduction
Learn about the Conversational Cloud Advanced Login options
Introduction
Introducing our advanced login system within the Conversational Cloud, seamlessly integrated with the robust Auth0 service (a subsidiary of Okta). This cutting-edge authentication solution incorporates a highly secure OAuth-based layer, meticulously implemented according to the latest industry standards while unlocking a plethora of product capabilities with confidence in state-of-the-art security.
Our advanced login system encompasses comprehensive in-product self-service screens, empowering you to effortlessly manage and customize your users' login experience within the Conversational Cloud. Take control and tailor the login process to align seamlessly with your unique requirements, all through user-friendly interfaces integrated into the system.
Self Service Portal
All advanced login capabilities and features are self-service and managed in a dedicated space within the Conversational Cloud.
Go to: Management Console -> Account Access Control
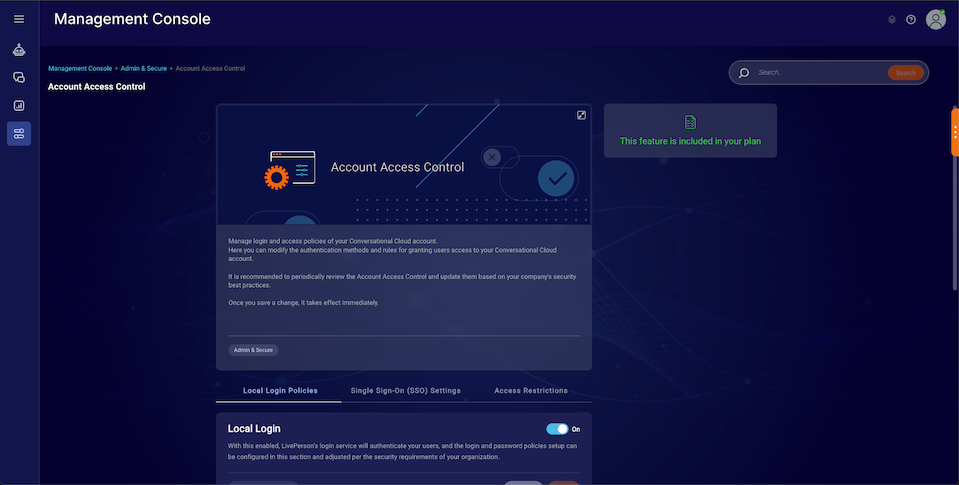
Offered Features
Local Login Policies
With this enabled, LivePerson’s login service will authenticate your users, and the login and password policies setup can be configured in this section and adjusted per the security requirements of your organization. If you switch the toggle off (assuming that you have at least one SSO connection enabled) your Local Login will be disabled. In this case users’ login and password policies will not be managed and enforced by LivePerson and all login flows will rely on your preferred SSO Identity Provider. Consequently, the change user password option will no longer be available under the User Management module.
General
- Deactivation of inactive users: Automatically deactivate an inactive user after a specified number of days. To be reactivated, the user must contact their admin.
- Max failed login attempts: Set the number of login failures a user is allowed before the account is locked.
- Multifactor Authentication: Activating this feature will require your users to login using two or more methods to authenticate. (Read more)
Password Policies
- Password strength: A strong password policy will make it difficult, if not impossible, for someone to guess a password through either manual or automated means.
The following options are available:- None: At least 1 character of any type.
- Low: At least 8 characters.
- Fair: (Default) At least 8 characters including a lower-case letter, an upper-case letter, and a number.
- Good: At least 8 characters including at least 3 of the following 4 types of characters: a lower-case letter, an upper-case letter, a number, a special character (such as !@#$%^&*).
- Excellent: At least 10 characters including at least 3 of the following 4 types of characters: a lower-case letter, an upper-case letter, a number, a special character (such as !@#$%^&*). Not more than 2 identical characters in a row (for example, 111 is not allowed).
- Password expiration: Automatically expire a password after a specified number of days.
- Prevent using previous passwords: Enabling this option disallows users from setting passwords that repeat passwords they’ve used in the recent past, up to a maximum of 24 entries per user. Note that when this option is enabled, only password changes going forward will be affected because the history will not have been kept prior to that point.
- Disallow commonly used passwords: Enabling this option disallows users from setting passwords to common options included in a default dictionary list.
- Password Policy Enforcement: With this enabled, password policy will be enforced on each login. This way you can make sure that your users will be forced to change their password if their current password does not apply with the latest account policy.
Single Sign-On (SSO) Settings
Set up Single Sign On Connections to provide your users with a seamless login experience using your company’s Identity Provider. They won’t have to enter their credentials again when accessing the Conversational Cloud.
- Set up the Identity Provider for SSO login to the Conversational Cloud
- SAML (SP-Initiated): Read the configuration guide
- OIDC (OpenID Connect): Read the configuration guide

2. Configure custom URLs (optional)
- Logout URL
- Error URL

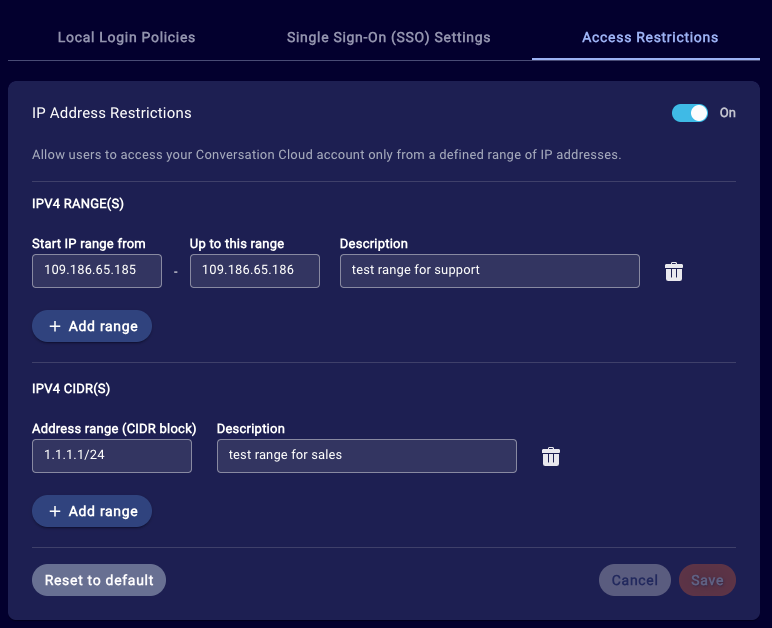
Access Restrictions
IP-Restriction
Allow users to access your Conversation Cloud account only from a defined range of IP addresses.
Advanced Login System - Q&A
How do I know if my account has been migrated to the advanced login system?
Go to https://authentication.liveperson.net/ and enter your account number and click 'Next'
On the next page, if the credentials widget contains 3 fields (Account number, Login name, Password), it means that you are using Legacy Login 🙁.
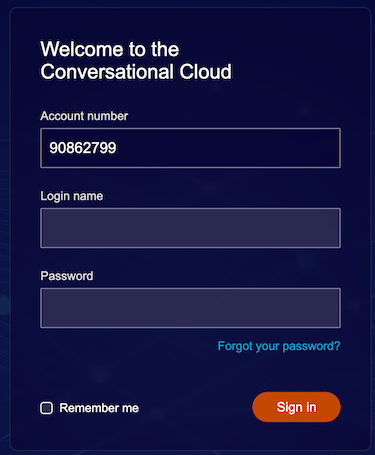
Legacy Login
Otherwise, if the widget shows only two fields (Login name and Password), it means that your account has already migrated to the advanced login system 🥳.
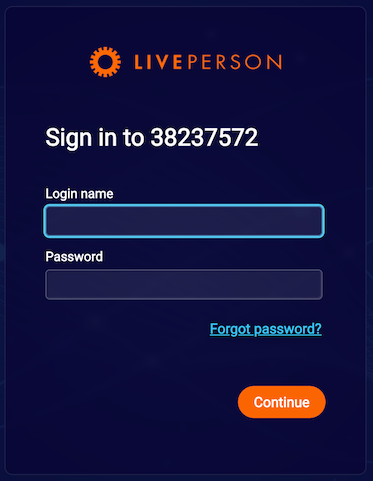
Advanced Login system
What should I do if my account is still on Legacy Login?
Please contact the LivePerson support team and ask to migrate your account to the Advanced Login system.
Missing Something?
Check out our Developer Center for more in-depth documentation. Please share your documentation feedback with us using the feedback button. We'd be happy to hear from you.